Yes, you can fight spam — part 1
Last week, I wrote about a study conducted by researchers at the University of California on the economics of spam. They had determined that the spammers were obtaining a conversion rate of less than one in twelve million from their botnet-sourced spam. That is, the spammers had to send twelve million spam emails for every customer they snagged.
I concluded that "just hit delete", educating the users, improved filters, or trying to use the legal system just were not going to work to stop spam.
This week, I'm going to talk about something that apparently does work: not tolerating the bad actors responsible.
If you follow spam issues in the news, then you may have heard of the takedown of a black-hat ISP in San Jose, California known as "McColo". You can read all about it in Brian Kreb's Washington Post article Major Source of Online Scams and Spams Knocked Offline.
In a nutshell, McColo was one of the prime bad-guys of the internet. Child porn, phishing, credit-card processing for criminals, you name it. We're talking the Dr. Moriarty of the internet here. As part of all that, they were knowingly hosting the command-and-control centers for major botnets.
McColo had been well-known to a number of internet security experts and spam-fighters. Attempts to get them disconnected by their upstream providers, Hurricane Electric and Global Crossing had long fallen on deaf ears. Finally, it reached the point where their support of McColo was going to reach a wider audience. Faced with a public shaming, they finally did the right thing and gave McColo the boot.
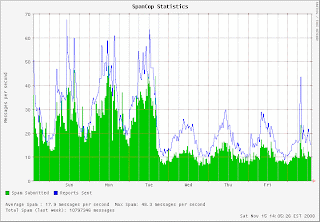
Here's what's significant: The shutdown of McColo resulted in a 60-70% drop in spam worldwide overnight.
Let me say that again: A 60-70% drop in spam overnight. Worldwide. From disconnecting just one bad actor.
This chart, courtesy of SpamCop shows it best:
Other spam-tracking sources are reporting similar reductions in spam. It is reported that detections of the Srizbi botnet (the biggest, at 60 billion spams/day) are down by up to 95%. Similar reductions in activity have been seen in several other botnets, including Mega-D, Bobax, Rustock and possibly Asprox.
I don't have any illusions that this drop is permanent. The spammers and bot-herders will be looking to rebuild their networks almost immediately. I've already noticed an increase in virus spam lately, as have others.
(Note: This may be a good time to remind your friends and relatives not to click on any attachments they receive — especially anything in a .zip file.)
Also unfortunately, McColo had a backup plan in the form of Swedish internet service provider TeliaSonera who, not knowing what was going on, left McColo connected to the internet. McColo was savvy enough to wait until the weekend before taking advantage of their backup connection. The problem was discovered within hours, but getting them disconnected again required CEO approval, which took even more time. All told, McColo was back online for about twelve hours. Enough time, unfortunately, to transmit botnet control updates to servers in Russia. More details can be found in the U.K. Register.
It will probably take time for the spammers to get the botnet up and running, but we should see spam levels begin to rise again shortly.
Other articles on this takedown:
I concluded that "just hit delete", educating the users, improved filters, or trying to use the legal system just were not going to work to stop spam.
This week, I'm going to talk about something that apparently does work: not tolerating the bad actors responsible.
If you follow spam issues in the news, then you may have heard of the takedown of a black-hat ISP in San Jose, California known as "McColo". You can read all about it in Brian Kreb's Washington Post article Major Source of Online Scams and Spams Knocked Offline.
In a nutshell, McColo was one of the prime bad-guys of the internet. Child porn, phishing, credit-card processing for criminals, you name it. We're talking the Dr. Moriarty of the internet here. As part of all that, they were knowingly hosting the command-and-control centers for major botnets.
McColo had been well-known to a number of internet security experts and spam-fighters. Attempts to get them disconnected by their upstream providers, Hurricane Electric and Global Crossing had long fallen on deaf ears. Finally, it reached the point where their support of McColo was going to reach a wider audience. Faced with a public shaming, they finally did the right thing and gave McColo the boot.
Here's what's significant: The shutdown of McColo resulted in a 60-70% drop in spam worldwide overnight.
Let me say that again: A 60-70% drop in spam overnight. Worldwide. From disconnecting just one bad actor.
This chart, courtesy of SpamCop shows it best:

Other spam-tracking sources are reporting similar reductions in spam. It is reported that detections of the Srizbi botnet (the biggest, at 60 billion spams/day) are down by up to 95%. Similar reductions in activity have been seen in several other botnets, including Mega-D, Bobax, Rustock and possibly Asprox.
I don't have any illusions that this drop is permanent. The spammers and bot-herders will be looking to rebuild their networks almost immediately. I've already noticed an increase in virus spam lately, as have others.
(Note: This may be a good time to remind your friends and relatives not to click on any attachments they receive — especially anything in a .zip file.)
Also unfortunately, McColo had a backup plan in the form of Swedish internet service provider TeliaSonera who, not knowing what was going on, left McColo connected to the internet. McColo was savvy enough to wait until the weekend before taking advantage of their backup connection. The problem was discovered within hours, but getting them disconnected again required CEO approval, which took even more time. All told, McColo was back online for about twelve hours. Enough time, unfortunately, to transmit botnet control updates to servers in Russia. More details can be found in the U.K. Register.
It will probably take time for the spammers to get the botnet up and running, but we should see spam levels begin to rise again shortly.
Other articles on this takedown:
- Washington Post: Major Source of Online Scams and Spams Knocked Offline
- Washington Post: A Closer Look at McColo
- HostExploit: McColo Cyber Crime USA (pdf)
- HostExploit: McColo Supplement (pdf) — details McColo's reconnection and Russian connections.
- Washington Post: Spam Volumes Drop by Two-Thirds After Firm Goes Offline
- Washington Post: Answers Trickle Out as Spammer Networks Remain Compromised
- UK Register: Dead network provider arms Rustock botnet from the hereafter — article about McColo's brief reconnection via Telia Sonera.

